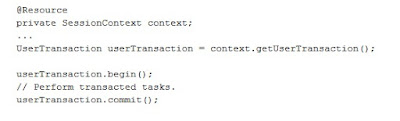
As the name suggests, a web service is a kind of webified application, that is, an application typically delivered over HTTP (Hyper Text Transport Protocol). A web service is thus a distributed application whose components can be deployed and executed on distinct devices.
Web services can be divided into two groups, SOAP-based and REST-style.
SOAP originally stood for Simple Object Access Protocol but, by serendipity, now may stand for Service
Oriented Architecture (SOA) Protocol. Whatever SOA may be, web services play a central role in the SOA approach to software design and development. For now, SOAP is just an XML (EXtensible Markup Language) dialect in which documents are messages. In SOAP-based web services, the SOAP is mostly unseen infrastructure. For example, in a typical scenario, called the request/response message exchange pattern (MEP), the client’s underlying SOAP library sends a SOAP message as a service request, and the web service’s underlying SOAP library sends another SOAP message as the corresponding service response. The client and the web service source code may provide few hints about the underlying SOAP.
Except in test mode, the client of either a SOAP-based or REST-style service is rarely a web browser but rather an application without a graphical user interface. The client may be written in any language with the appropriate support libraries. Indeed, a major appeal of web services is language transparency: the service and its clients need not be written in the same language. Language transparency is the key to web service
interoperability; that is, the ability of web services and requesters to interact seamless despite differences in programming languages, support libraries, and platforms.
If a SOAP-based web service written in Java can have a Perl or a Ruby consumer, there must be an intermediary that handles the differences in data types between the service and the requester languages.
XML technologies, which support structured document interchange and processing, act as the intermediary. For example, in a typical SOAP-based web service, a client transparently sends a SOAP document as a request to a web service, which transparently returns another SOAP document as a response.
Calculator Web Service Example:
This is a simple SOAP web service that exposes four methods that are the main calculation operation. All the required libraries to compile, execute and consume Web Services are part of Standard Java 6, that supports JAX-WS (Java API for XML-Web Services).
A SOAP-based web service could be implemented as a single Java class but, following best practices, there should be an interface that declares the methods, which are the web service operations, and an implementation, which defines the methods declared in the interface. The interface is called the SEI: Service Endpoint Interface. The implementation is called the SIB: Service Implementation Bean. The SIB can be either a POJO or a Stateless Session EJB (Enterprise Java Bean).
The picture below shows the SEI (Service Endpoint Interface) for the Calculator Web Service.
It exposes the four web service's methods: add, substract, multiply, divide.
The annotation @WebService signals that this is the SEI (Service Endpoint Interface).
@WebMethod signals that each method is a service operation.
The @SOAPBinding annotation impacts the under-the-hood construction of the service contract, the WSDL (Web Services Definition Language) document. In my interface I used default values for this annotation, so it could be omitted. It specifies message style (DOCUMENT or RPC), encoding (LITERAL or SOAP ENCODED) and parameter style (WRAPPED or BARE).
Next picture shows the SIB (Service Implementation Bean) that implements the methods listed by the previous interface:
The @WebService property endpointInterface links the SIB (this class) to the SEI (com.faeddalberto.calculator.CalculatorWSImpl). Note that the method implementations are not annotated as @WebMethods because those were already defined as web service methods in the interface.
The two files are compiled in the usual way from the current working directory, which in this case is immediately above the subdirectory "com". The symbol % represents the command prompt:
% javac com/faeddalberto/calculator/*.java
Now that we
have successful compiled our web service we need to invoke, from the working
directory, the wsgen utility that comes
with Java 6:
% wsgen –cp .
com.faeddalberto.calculator.CalculatorWSImpl
This utility generates some artifacts: java types needed by the Endpoint.publish to generate
the service’s WSDL.
The simplest way to publish a web service in a
development/test environment is using a simple Java SE Application.
This application publishes the web service whose SIB is
com.faeddalberto.calculator.CalculatorWSImpl. For now, the service is published
at network address 127.0.0.1., which is localhost, and the publication path is
/calculator, an arbitrary name.
The Endpoint class has an overloaded publish method. In this two-argument
version, the first argument is the publication URL as a string and the second
argument is an instance of the service SIB, in this case com.faeddalberto.calculator.CalculatorWSImpl.
The application runs indefinitely, awaiting service requests. It needs to
be terminated at the command prompt with control-C or the equivalent.
Once the applicatation is started, open a browser
to the URL http://127.0.0.1/calculator?wsdl to view the service contract, the WSDL
document. This is an easy test to determine whether the service has deployed
successfully. If the test succeeds, a client then can be executed against the
service.
If everything is going well during the web service publication, you will see the following WSDL (Web Service Descriptor Language) on your browser page:
In one of my next posts I'll describe the various parts of an WSDL document.
Associated to the Web Service contract there is also an XSD document describing the types for every request and response. If you open a browser to the URL http://127.0.0.1/calculator?xsd=1 you can see this:
The types defined by the previou XSD are add, substract, multiply and divide (for the requests) and the same type name with the string Response attached for the web service responses.
If you scroll above in the post you'll see that the wsgen utility used to create artifacts has created these types as Java classes: it means that that utility uses JAX-B to create java types associated to xsd elements needed by the web service to create the WSDL document and to marshal and unmarshal requests and responses.
In full production mode, a Java Application Server such as BEA WebLogic, GlassFish, JBoss, or WebSphere might be used. To deploy our web service into an application server we need to create the WAR (Web Archive), and to do so we need to invoke the jar utility:
% jar cvf calculator.war WEB-INF
in which calculator.war is the name of the war we are creating and WEB-INF is the folder into which we have our class files to put into the war. Once created we can deploy it in the application server we choose and restart it. As we've done with our simple Jave SE application, once the applicatation server is started, open a browser to the URL http://127.0.0.1/calculator?wsdl to view the service contract, the WSDL document. This is an easy test to determine whether the service has deployed successfully.
Now that we have
our web service up and running its time to call it and verify that it works.
We need now to
create a web service client, and we can do it in different ways.
I show you a
dynamic client and a static client both developed as a simple Java SE
application but the same clients could also be used in a Java EE application
Servlet or another utility class.
Dynamic client:
The first client I
show you Is the dynamic solution:
This java class
uses a URL object with a query string pointing to the WSDL location.
It then creates an
XML qualified name, which has the syntax namespace
URI:local name. A URI is
a Uniform Resource Identifier and differs from the more common URL in that a
URL specifies a location, whereas a URI need not specify a location. In short,
a URI need not be a URL. In this example, the namespace URI is provided in the
WSDL, and the local name is the SIB class name CalculatorWSImpl
with the word Service appended. The local name occurs in the service section, the last section of the WSDL document.
Once the URL and QName objects have been constructed
and the Service.create method has been invoked, the
statement of interest:
CalculatorWS calculator =
service.getPort(CalculatorWS.class);
executes. In the WSDL document, the portType section describes, in the style of an interface, the
operations included in the web service. The getPort method returns a reference to
a Java object that can invoke the portType operations. The port object reference is of type com.faeddalberto.calculator.CalculatorWS, which is the
SEI type.
The Java client invokes the
web service methods; and the Java libraries generate and process the SOAP messages
exchanged transparently to enable the successful method invocations.
Static client:
In this section we
will develop a standalone, static web service client to the Calculator web
service
developed above. First all the static artifacts needed are generated using
the wsimport tool. Note that the Calculator web service must be running
when generating the artifacts, in order for wsimport to be able to access the
WSDL document of the service.
% wsimport -p
com.faeddalberto.calculator.staticclient -keep http://127.0.0.1/calculator?wsdl
This utility generates various classes in the subdirectory com.faeddalberto.calculator.staticclient (the
-p flag stands for package). These classes make it easier to write a client
against the service.
The list of the generated artifacts:
Three points about these generated source files deserve mention. First, the interface CalculatorWS declares the very same methods as the original SEI. The methods are the web service operation add, substract, multiply, divide. Second, the class CalculatorWSImplService has a no-argument constructor that constructs the very same Service object as the original Java client DynamicCalculatorClient. Third, CalculatorWSImplService encapsulates the getcalculatorWSImplPort method, which returns an instance of type CalculatorWS, which in turn supports invocations of the four web service operations. Together the two generated types, the interface CalculatorWS and the class CalculatorWSImplService, ease the task
of writing a Java client against the web service. Next picture shows a client that uses the client-support code from the wsimport utility:
This client is functionally equivalent to the previous, but this client is far easier to write. In particular, trouble some yet critical details such as the appropriate QName and service endpoint now are hidden in the wsimport-generated class. The idiom that is illustrated here works in general for writing clients with help from WSDL-based artifacts such as CalculatorWS and CalculatorWSImplService:
- First, construct a Service object using one of two constructors in the wsimport generated class, in this example client.CalculatorWSImplService. The no-argument constructor is preferable because of its simplicity. However, a two-argument constructor is also available in case the web service’s namespace (URI) or the service endpoint (URL) have changed. Even in this case, however, it would be advisable to regenerate the WSDL-based Java files with another use of the wsimport utility.
- Invoke the get...Port method on the constructed Service object, in this example, the method getCalculatorWSImpllPort. The method returns an object that encapsulates the web service operations declared in the original SEI.
Next picture shows the result for this client:
This was just a simple web service. There are different other ways of writing web services and clients against them, I'll show you on my next posts.